The SSL VPN feature (also known as WebVPN) provides support for remote user access to enterprise networks from anywhere on the Internet. Remote access is provided through a Secure Socket Layer- (SSL-) enabled SSL VPN gateway. The SSL VPN gateway allows remote users to establish a secure Virtual Private Network (VPN) tunnel using a web browser. This feature provides a comprehensive solution that allows easy access to a broad range of web resources and web-enabled applications using native HTTP over SSL (HTTPS) browser support.
What is SSL?
Secure Sockets Layer is a protocol developed by Netscape for transmitting private documents via the Internet. SSL uses a cryptographic system that uses two keys to encrypt data – a public key known to everyone and a private or secret key known only to the recipient of the message.
SSL VPN delivers three modes of SSL VPN access:
- Clientless: Clientless mode provides secure access to private web resources and will provide access to web content. This mode is useful for accessing most content that you would expect to access in a web browser, such as Internet access, databases, and online tools that employ a web interface.
- Thin Client (port-forwarding Java applet): Thin client mode extends the capability of the cryptographic functions of the web browser to enable remote access to TCP-based applications such as Post Office Protocol version 3 (POP3), Simple Mail Transfer Protocol (SMTP), Internet Message Access protocol (IMAP), Telnet, and Secure Shell (SSH).
- Tunnel Mode: Full tunnel client mode offers extensive application support through its dynamically downloaded Cisco AnyConnect VPN Client (next-generation SSL VPN Client) for SSL VPN. Full tunnel client mode delivers a lightweight, centrally configured and easy-to-support SSL VPN tunneling client that provides network layer access to virtually any application.
There are few steps to set up an SSL VPN:
- Configure a trust point
- Create an account
- Configure WebVPN
- Test WebVPN
Example
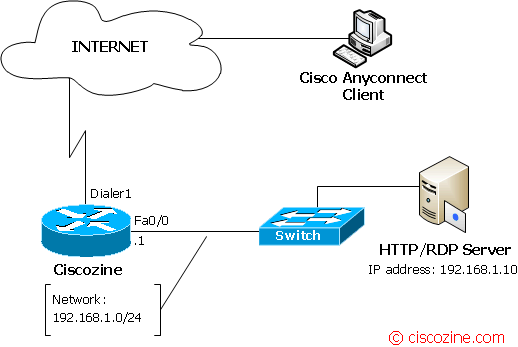
In this example, there’s a VPN SSL server with tunnel mode and thin client functionality. The WebVPN service is listening to the address https://[dialer1_ip_address].
1. Configure a trust point
Create your rsa keys:
Ciscozine(config)#crypto key generate rsa label ciscozine-rsa modulus 2048
then, if you have not a CA, create your local pki (used by the SSL server)
Ciscozine(config)#crypto pki trustpoint my-ciscozine-ca Ciscozine(ca-trustpoint)#enrollment selfsigned Ciscozine(ca-trustpoint)#subject-name cn=Ciscozine Ciscozine(ca-trustpoint)#rsakeypair ciscozine-rsa
and to obtain the certificate for your router from the local certificate authority:
crypto pki enroll my-ciscozine-ca
The system will ask you some questions; choose what you prefer, but it is important to response “yes” to the last question “Generate Self Signed Router Certificate?”.
Note: If you would more info about self-signed certificates read this article.
2. Create an account
For security, it is recommended to create an account without privilege:
username ciscozine privilege 0 secret myt3ST
3. Configure WebVPN
3.a Configure the gateway properties
The gateway defines the basic network and cryptographic settings of the SSL VPN server.
Create a gateway named ‘ciscozine_gw’, link it to the dialer1 and select the trustpoint to use (in this example, the ‘my-ciscozine-ca’). The ‘inservice’ command is required to enable the webvpn functionality.
Ciscozine(config)#webvpn gateway ciscozine_gw Ciscozine(config-webvpn-gateway)#ip interface Dialer1 port 443 Ciscozine(config-webvpn-gateway)#ssl trustpoint my-ciscozine-ca Ciscozine(config-webvpn-gateway)#inservice
3.b Configure the context properties
The context defines portal customization, url list (for the clientless features), port forwarding list (for the thin client), the AAA properties and so on.
Define a url-list and a port-forwarding list (to access to the RDP/HTTP server); then link this context to the ‘ciscozine_gw’ gateway and enable the “ciscozine-ctx” context using the “inservice” command.
Ciscozine(config)#webvpn context ciscozine-ctx Ciscozine(config-webvpn-context)#url-list "my-url-list" Ciscozine(config-webvpn-url)#heading "My-website" Ciscozine(config-webvpn-url)#url-text "ciscozine" url-value "https://www.ciscozine.com" Ciscozine(config-webvpn-url)#url-text "Test-http-server" url-value "http://192.168.1.10" Ciscozine(config-webvpn-context)#port-forward "my-website" Ciscozine(config-webvpn-port-fwd)#local-port 3390 remote-server "192.168.1.10" remote-port 3389 description "my-rdp" Ciscozine(config-webvpn-context)#aaa authentication list login-for-vpn Ciscozine(config-webvpn-context)#gateway ciscozine_gw Ciscozine(config-webvpn-context)#inservice
3.c Configure the policy group
In the policy groups are applied properties like url-list, port-forwarding list, SVC configuration (for the tunnel mode client) and so on.
Apply the url-list and the port-forward list defined in the previous step (3.b Configure the context properties). Configure the SSL VPN Client (SVC) to allow the remote access for the network 192.168.1.0/24.
Ciscozine(config-webvpn-context)#policy group ciscozine_policy Ciscozine(config-webvpn-group)#url-list "my-url-list" Ciscozine(config-webvpn-group)#port-forward "my-website" Ciscozine(config-webvpn-group)#functions svc-enabled Ciscozine(config-webvpn-group)#svc address-pool "VPN-SSL-POOL" Ciscozine(config-webvpn-group)#svc keep-client-installed Ciscozine(config-webvpn-group)#svc split include 192.168.1.0 255.255.255.0
Define the default group policy:
Ciscozine(config-webvpn-context)#default-group-policy ciscozine_policy
Specify the IP pool addresses used by the Cisco SSL VPN client interface:
ip local pool VPN-SSL-POOL 192.168.100.1 192.168.100.5
3.d Install the Cisco Anyconnect
The Cisco Anyconnect is the client used for the tunnel mode feature and it depens by the platforms used. For the Windows, MacOS or Linux operative systems, the client could be saved into the router, so when a client tried to start a full tunnel mode, the Vpn client will be downloaded automatically.
To install the SVC for windows platform, download the client from the Cisco site, upload into your router and install in the ‘webvpn’ folder.
webvpn install svc flash:/webvpn/anyconnect-dart-win-2.5.3055-k9.pkg sequence 1
4. Test WebVPN
Open your https page, log in (using the ‘ciscozine’ account created in the second step) and check the three functionality:
- Clientless: click the url list to check how it works
- Thin client: enable thin client feature (an applet java). If you use Windows, test it using the command: mstsc /v 127.0.0.1:3389
- Full client: install the client and check if
- you can ping a remote host, for instance: ping 192.168.1.10
- you can see the 192.168.1.10 webpage
Remember: To enable a SSL VPN gateway or context process, use the inservice command in webvpn gateway configuration or webvpn context configuration mode. To disable a SSL VPN gateway or context process without removing the configuration from the router configuration file, use the no form of this command.
Restrictions of CiscoAnyConnect VPN Client:
- Datagram Transport Layer Security (DTLS) with SSL connections
- Standalone Mode
- IPv6 VPN access
- Compression support
- Language Translation (localization)
- Client-side authentication
- Adaptive Security Appliance (ASA) and Adaptive Security Device Manager (ASDM) and any command-line interface (CLI) associated with the them
- Adjusting Maximum Transmission Unit (MTU) size
- Sequencing
Remember: You can use your smartphone as a VPNSSL Client! For more info check the “Cisco AnyConnect Secure Mobility Client” functionality.
References: http://www.cisco.com/…/12_4t11/htwebvpn.html

Thanks for the help, there were additional commands in here that I was not using to make my SSL-VPN from working. I believe everytime I would reboot the router it would loose the certificate. I plan to try test this next downtime.
Your site is also filled with tons of details that I love to read about. Thanks again.
very informative. I was looking for this kind of document
hi sir ,if don;t configure split tunnel.the vpn user how to pass vpn access internet.
If you want internet access through cisco anyconnect vpn client, you have to take out svc split commands and add interface that accepts vpn client traffic to nat inside policy. In my case I have c1921 router.
here is the config without the gateway part:
interface Virtual-Template1
ip unnumbered GigabitEthernet0/1
ip nat inside
ip virtual-reassembly in
!
webvpn context Cisco-WebVPN
virtual-template 1
aaa authentication list default
gateway vpngateway
!
policy group webvpnpolicy
functions svc-enabled
functions svc-required
svc address-pool “vpnpool” netmask 255.255.255.0
svc keep-client-installed
svc dns-server primary 192.168.1.1
default-group-policy webvpnpolicy